New variant of “Nyetya” Ransomware compromises systems worldwide
Clients of Cisco they are protected against Nyetya. New variant of "Nyetya" Ransomware compromises systems worldwide
This article provides information to help detect virus behavior. Cisco Talos studies their behavior and presents the tools to mitigate these risks.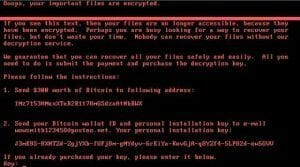
Malware functionality
In our research on this ransomware variant, Talos observed that compromised systems have a file called "Perfc.dat". Perfc.dat contains the functionality needed to further compromise the system and contains a single unnamed export function named # 1. The library tries to obtain administrative privileges (SeShutdowPrivilege and SeDebugPrivilege) for the current user through the Windows API AdjustTokenPrivileges. If successful, the ransomware will overwrite the Master Boot Record (MBR) on the disk drive named PhysicalDrive 0 within Windows. Regardless of whether the malware succeeds in overwriting the MBR or not, it will then proceed to create a scheduled task via schtasks to reboot the system one hour after infection. As part of the propagation process, the malware enumerates all machines visible on the network through NetServerEnum and then looks for an open TCP port 139. This is done to compile a list of devices that expose this port and can possibly be compromised. Malware has three mechanisms used to spread once a device is infected: EternalBlue - the same feat used by WannaCry. Psexec - A legitimate Windows administration tool. WMI - Windows Management Instrumentation, a legitimate Windows component. These mechanisms are used to try to install and run perfc.dat on other devices to spread laterally. For systems that have not applied MS17-010, the EternalBlue exploit is exploited to compromise systems. We have written about this previously in our WannaCry coverage. Psexec is used to execute the following statement (where wxyz is an IP address) using the Windows token of the current user to install the malware on the network device. Talos is still investigating the methods by which the "current user's Windows token" is retrieved from the machine. C: \ WINDOWS \ dllhost.dat \\ wxyz -accepteula -s -d C: \ Windows \ System32 \ rundll32.exe C: \ Windows \ perfc.dat, # 1 WMI is used to run the following command that performs the same function as above, but using the username and password of the current user (such as username and password). Talos is still investigating how credentials are retrieved from the machine at this time. Wbem \ wmic.exe / node: "wxyz" / user: "username" / password: "password" "process call create" C: \ Windows \ System32 \ rundll32.exe \ "C: \ Windows \ perfc.dat \" #1" After a system is successfully compromised, the malware encrypts files on the host using RSA 2048-bit encryption. Additionally, the malware cleans up the event logs on the compromised device using the following command: wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application & fsutil usn deletejournal / D% c:Coverage
Clients of Cisco are protected against Nyetya through the following products and services. Advanced Malware Protection (AMP) it is ideal for preventing the execution of the malware used by these threat actors. Network security devices such as NGFW, NGIPS, and Meraki MX can detect malicious activities associated with this threat. AMP Threat Grid helps identify malicious binaries and build protection across all Cisco Security products. Email and the web have not been identified as an attacking vector at this time. Also, there are no known C2 items related to this malware at this time. Customers of the Snort Open Source Subscriber Ruleset can stay up-to-date by downloading the latest rule pack available for purchase at Snort.org. See the full original news: http://blog.talosintelligence.com/2017/06/worldwide-ransomware-variant.htmlShare this post
Publications
related
User protection Don’t let it keep you awake at night!
In today's hyper-connected world, we need a proactive and dynamic zero-trust security approach that adapts to the evolving threat landscape and the increasing complexity of modern IT environments without slowing down your organizational innovation. The user protection suite that Solutel provides, as an expert in cybersecurity solutions, protects against all...
Solutel at the 8th edition of Emplea Tech 2024
Solutel has been present at the 8th edition of Emplea Tech, the technology employment forum organized by Tajamar Tech, the technology section of Tajamar. The largest Tech attraction event, where students of VET, University and Master of Madrid have the opportunity to get in contact with leading technology companies that are...
Solutel, one more year, bets on the celebration of its internal Kick Off
Solutel, one more year, bets on the celebration of its internal Kick Off. Solutel has been celebrating its internal Kick Off for more than 15 years. Weekend dedicated to fostering team collaboration and getting to know each other better. What are the benefits for Solutel of holding the Kick Off? Align...
Solutel wishes you Happy Holidays!
Having you on board is the foundation of our success. Once again, thank you for trusting SOLUTEL! As we enter 2024, let's toast to opportunities and successes together, and to all the good things to come. Our greatest wish is that all your projects are fulfilled, and the SOLUTEL team will be...








